Before the days ofElectraand unc0ver dawned upon us, there wasYalu, an iOS 10-centric jailbreak too by the talented hacker Luca Todesco (@qwertoruiopz); but apartfrom a few teasers here and there, the jailbreak community hasn’t heard much him since the Yalu days – that is, until now.
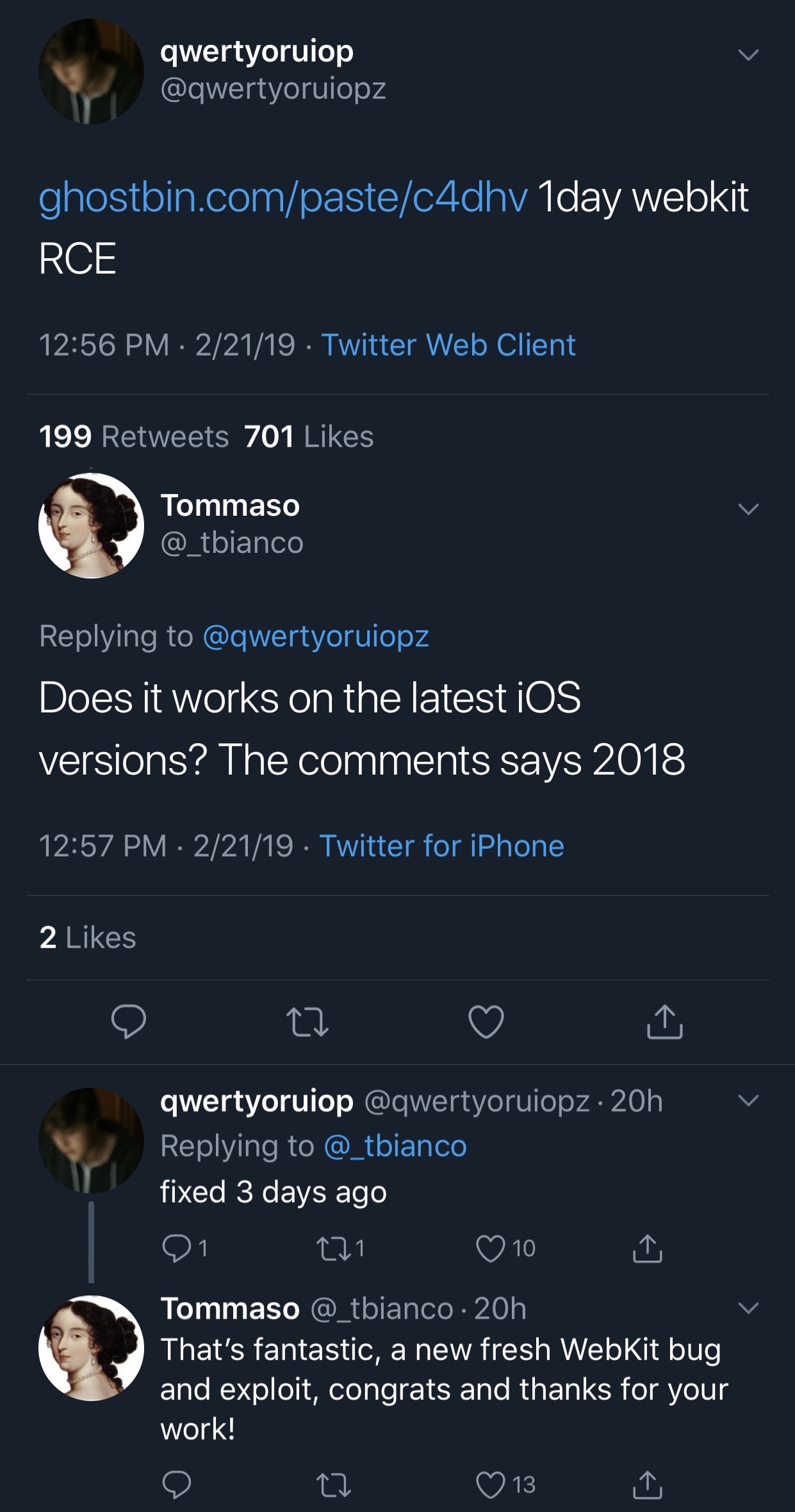
In a bombshell Tweet shared this week, Todesco released what appears to be a WebKit-based exploit that allows remote code execution (RCE) in web browsers with JIT. What’s more is that the exploit was only just fixed three days ago, which means it should be viable on all versions of iOSup to Apple’s latest release – 12.1.4:

Todescopublished a proof of concept on GhostBin, permitting the public to study the exploit and use it as they see fit.
It’s not every day that a WebKit exploit makes itself known, but they have a long history in the jailbreak community. For example,an ancient jailbreak tool called JailbreakMeby Comex utilized a similar exploit (along with others) to allow jailbreaking directly from theSafariweb browser when the user visited a specific website and interacted with it.
It remains to be seen if a similar JailbreakMe-stylejailbreakwill materialize from Todesco’s new exploit, but it certainly gives veteran jailbreakers such as myself a nostalgic trip down memory lane.
In the meantime, hacker andunc0verlead developer Pwn20wndcontinues to work diligently on his iOS 12 jailbreakfor iOS 12.0-12.1.2. This is a semi-tethered jailbreak and will only support certain devices when the initial public beta is released; support for additional devices, including A12, will be added at a future date.
Are you excited about all the recent iOS 12-oriented exploits that have been released as of late? Share your thoughts in the comments section below.